CVE-2023-23397 Threat Overview
InsiderSecurity carries out research and analysis on the latest cyber threats to help organizations stay ahead. InsiderSecurity analysed the possible exploitation techniques for the recent Outlook vulnerability, as well as methods for early detection of such exploits, both for this specific vulnerability and future similar vulnerabilities. The following are our findings:
Microsoft recently released a patch for Outlook vulnerability CVE-2023-23397, which has been actively exploited for almost an entire year. The CVE-2023-23397 vulnerability in Microsoft Outlook has generated significant concern due to its high severity score of CVSS 9.8. It affects everything from Microsoft 365 apps for enterprise to Outlook 2013 SP1. This exploit has caught the attention of a hacking group linked to Russia’s GRU military intelligence agency that is using it to target some European organizations in government, transportation, energy, and military sectors.
Companies have to quickly patch their Outlook software and implement measures to detect if they have been compromised. As companies may already be compromised, it is not sufficient to simply block access to port 445 on the internet.
Stealing the Net-NTLM hash
CVE-2023-23397 allows the attacker to steal the Net-NTLM hash from the victim, which enables an attacker to assume a victim identity and to move deeper into the organisation.
The attacker steals the Net-NTLM hash by tricking the victim into accessing an UNC path \\Attacker_IP_Address. The ‘leaking’ of Net-NTLM hash through this mechanism is not new, nor is it considered an actual vulnerability by itself, as it is a feature which allows Windows machines to communicate with one another.
The safer Kerberos authentication is typically used by machines within the same domain. However, when a user wants to communicate with a machine belonging to a different domain or with a machine known only by its IP address, the Kerberos authentication would not work, hence, the user’s authentication type will be downgraded from Kerberos to NTLM, and the user’s Net-NTLM hashes will automatically be sent to the destination.
For instance, if a user attempts to access the following UNC paths, the Net-NTLM hash will be sent (and therefore leaked) to an attacker.
\\Attacker_IP_address
\\Attacker_hostname.In_another_domain
How is CVE-2023-23397 exploited
The impact of CVE-2023-23397 is equivalent to the impact of a successful Net-NTLM based attack. In all attack paths, the attacker sends a malicious email to the victim, causing the victim’s machine to send their Net-NTLM hash to the attacker. Once the attacker steals the Net-NTLM hash from the victim, they could proceed with either of the attacks described in the slides:
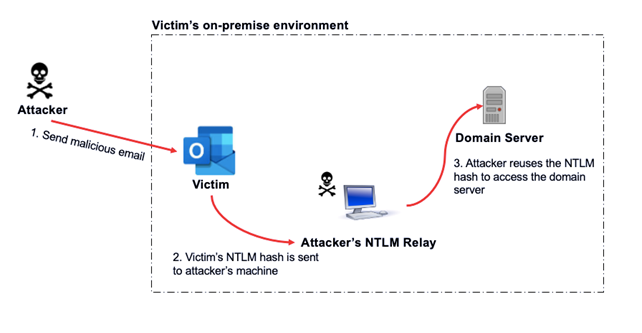
- In attack path 1, the attacker could gain high privileged access to Windows domain server of interest by relaying the Net-NTLM of the privileged user to the domain server. This could be done by targeting a privileged user to send their Net-NTLM hash to a pre-compromised machine belonging to a clueless employee within the network. This is also known as NTLM-Relay attack.
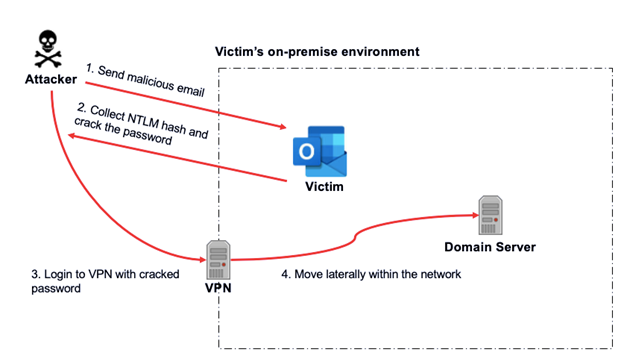
- In attack path 2, the attacker could attempt to recover the password from the stolen Net-NTLM hash through offline password cracking, allowing the attacker to login into the company’s network via VPN and move laterally from assets to assets. This could work because the password for all the services available to the victim could be synchronized and centrally managed by an identify provider (i.e. – Domain controller). Multi-factor authentication (MFA) will reduce the possibility of this attack path.

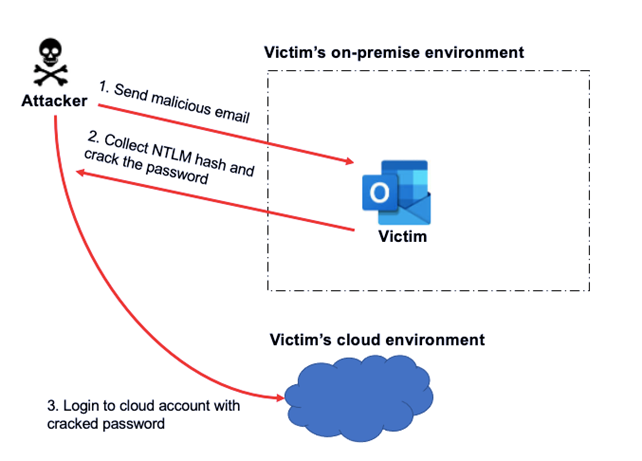
- In attack path 3, the same password recovery technique described in attack path 2 would be used which allows the attacker to login into the victim’s cloud account. The attack could then continue to search for valuable data or secrets stored in the cloud and perform cloud-based attacks. MFA will reduce the possibility of this attack path too.

Detection strategies
There are a number of approaches to detect successful Net-NTLM based exploits due to the CVE-2023-23397 or similar vulnerabilities. These include
1. Detecting for TCP connections made to port 445 (SMB) and port 80 (WebDAV) in both internal (Attack path 1) and external IP (Attack path 2 and 3) addresses, especially for new destination IP addresses not observed in the past.
2. Successful login from accounts made from a new location, whether from cloud and on-premise (Attack paths 1,2 and 3).
3. Detecting for NTLM authentication from accounts that do not usually perform NTLM authentication. Successful Net-NTLM-Relay attack has been observed to be chained with NTLM hash dump which will lead to pass-the-hash attack.
4. Monitoring for changes in server access patterns, where a compromised account is used to access servers in a suspicious manner.
Behaviour analytics can detect such changes and enable users to detect Net-NTLM exploits, even if the exploit is due to newly discovered vulnerability.
The above are some of the use cases we have in InsiderSecurity solutions, and we hope these tips are useful for the community. So, gear up and get ready to hunt down these attacks like a pro. And always remember to stay safe out there!
Avoid Similar Attacks with InsiderSecurity
Looking for ways to stay ahead of any cyber threats? InsiderSecurity provides advanced cybersecurity behavior analytics products that help your company to uncover cyber threats before there is any serious data loss. We offer a range of solutions, including Automated UEBA for securing on-premise and cloud IT infrastructure, as well as the Cloud Security Monitor for ensuring cloud data security.
Automated UEBA establishes baselines of data access behaviour and alerts on abnormal activity. It detects insider threats, backdoors and advanced attacks by leveraging machine learning and advanced user behavioral analytics.
InsiderSecurity protects your critical data wherever it resides—on-premises, in the cloud and the hybrid environment.





