Introduction
In today’s digital age, cybersecurity is of paramount importance, with organizations facing an ever-evolving landscape of cyber threats and attacks. InsiderLab (our team of cybersecurity experts) conducts in-depth research and analysis of historical and emergent cyber threats, empowering organizations with the foresight needed to proactively safeguard their digital landscapes.
Amid recent events, the InsiderLab team has scrutinized the tactics and exploitation methods employed by high-profile threat actors. Through tireless investigations, InsiderLab has uncovered critical insights that shed light on the world of cyber threats. These findings not only raise awareness but also provide a comprehensive understanding of the evolving threats that organizations face today.
In this report, we focused on high-profile attacks, particularly those involving compromised Microsoft 365 accounts and studied the tactics used by these attackers. Each case study provides a unique window into the world of cyber threats, offering insights into the cunning methods employed by cyber adversaries and the vulnerabilities they exploit. Furthermore, InsiderLab released a free tool to aid in identifying similar classes of attacks.
Case study 1: Microsoft Storm-0558 SaaS breach
Uncovered in 2023, the threat actor behind the STORM-0558 attacks successfully accessed their victim’s Microsoft Exchange Online and Outlook accounts, completely bypassing 2FA (two-factor authentication). Notably, various U.S. government entities endured the brunt of the STORM-0558 onslaught.
These attackers were known to conduct their activity behind the SoftEther proxy VPN service, thereby masking their true IP addresses.
This was uncovered eventually discovered when the victims’ Microsoft 365 audit logs revealed that an unusual application was used to access the emails. In the blog provided by CISA (Cybersecurity and Infrastructure Security Agency), it was reported that the log entry for the ‘MailItemsAccessed‘ operations contained an unusual AppID. While it is difficult to define what is unusual, keeping track of what is typical would be useful in detecting these deviations.
For example, if the user typically uses the Outlook Express email client or Outlook.com to access their emails, a log entry with an unusual AppID (application identities) would attribute the access to a different application type, indicating a deviation in email access behavior.
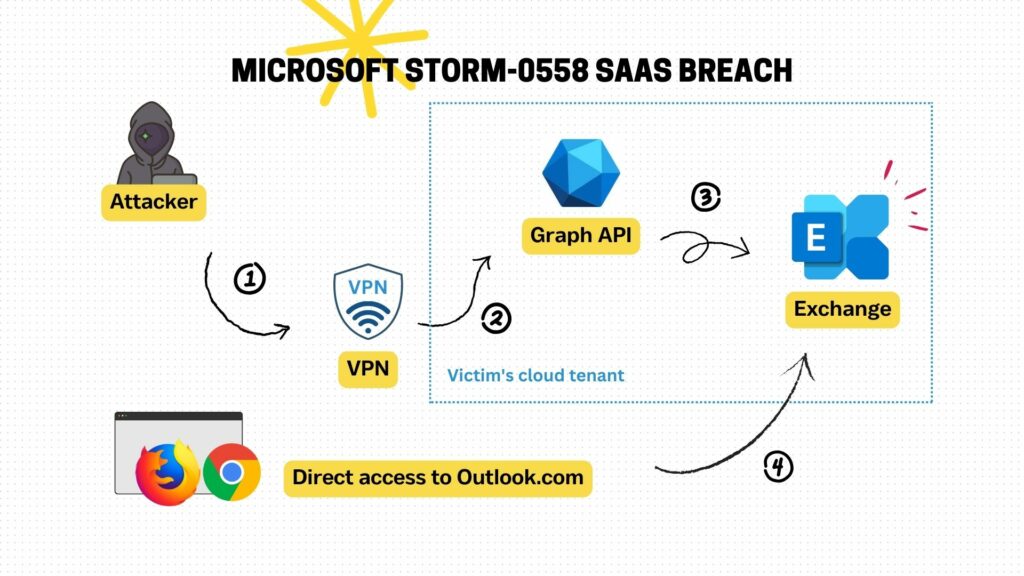
The following illustration shows the difference between a threat actor and a legitimate user in accessing Exchange Online. The threat actor uses additional services such as a VPN and the Microsoft Graph API as shown in steps 1 to 3, while the legitimate user typically only uses a web browser as shown in step 4. This approach taken by the threat actor leaves an unusual AppID and client IP address in the audit trail.
Case study 2: SolarWinds SUNBURST attack
Moving on to another case study, we will discuss the SolarWinds SUNBURST Attack. Uncovered in 2020, the threat actor behind the SUNBURST attacks leveraged the Microsoft Graph API to perform data exfiltration. This SUNBURST attack impacted various government entities and major players within the technology sector.
The attackers searched for existing cloud applications with email access privileges, or alternatively, escalated the permissions of pre-existing applications. This cunning maneuver is meticulously documented in this research article , spotlighting the attacker’s utilization of the ‘Mail.ReadWrite’ permission within an existing cloud application to gain access to victim email content via said application.
Furthermore, an alternate strategy observed in a separate attack involved the dispatch of phishing emails by attackers. These deceitful communications were tailored to dupe victims into unwittingly granting consent to install malicious cloud applications. If the victim falls for this trick, attackers would be able to access the victim’s email and files via the malicious cloud application.
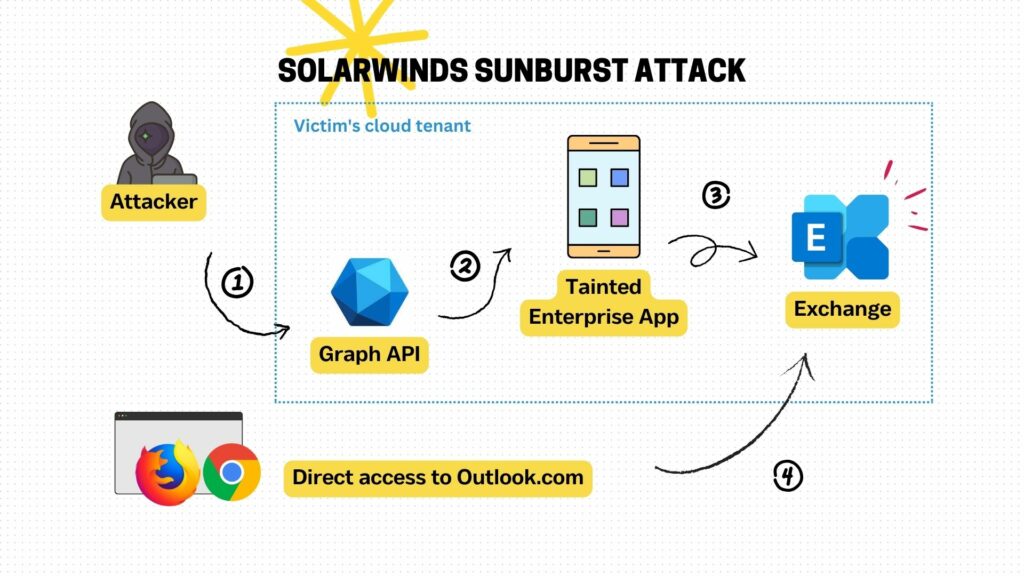
The following illustration describes the additional services such as the Graph API and the tainted enterprise application. The attacker would access victims’ emails as shown in step 1 to step 3, whereas the legitimate user would simply access the email directly via a web browser as shown in step 4. The attacker’s approach leaves an unusual AppID in the audit trail.

Case study 3: LAPSUS$ attacks
Now we turn to the LAPSUS$ Attacks, discovered in 2022. The attacker behind this mysterious name targeted many victims, including major tech companies. The attacker is known to access cloud resources via a VPN. A comprehensive account of this method is described in this Microsoft report, where the threat actor employs NordVPN as their conduit to hide their true IP addresses.
The attacker also added an email transport rule to forward emails from their victims to their own account.
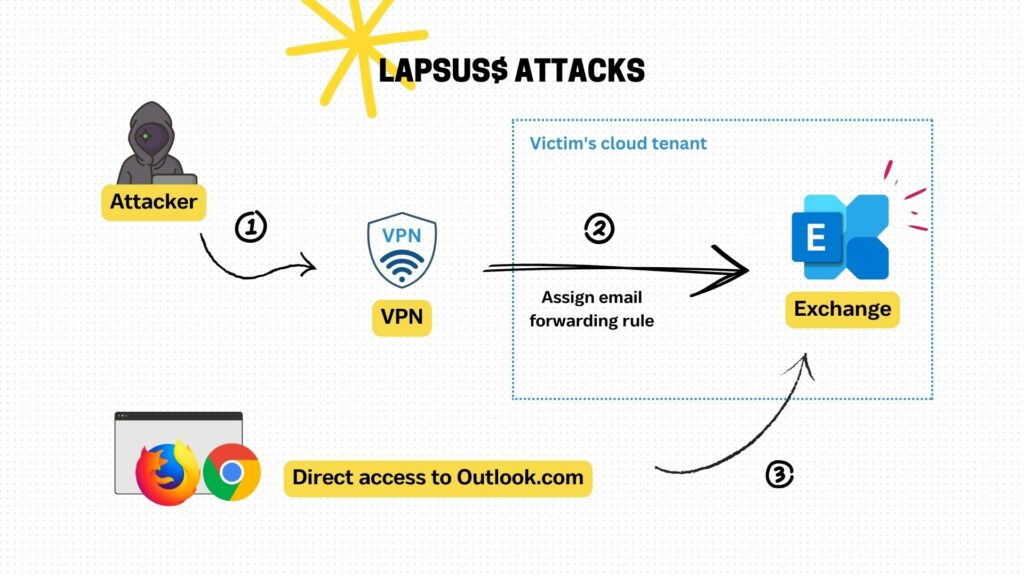
The following illustration describes additional services such as the VPN service the attacker would use to access victims’ emails as shown in step 1 to step 2. The attacker’s approach leaves an unusual client IP in the audit trail.

Threat detection with CASUAL tool for compromised accounts


Given the ongoing high-profile breaches in Microsoft 365, our team is proud to introduce CASUAL (CloudAuditSearchUAL) —a user-friendly tool designed to uncover hidden cyber anomalies in the audit trail. Download CASUAL here.
CASUAL analyzes log entries in the Microsoft 365 Unified Audit Log (UAL) and produces a JSON file that contains the following information about accesses to Microsoft 365:
- Unique geolocations
- Unique application identities (AppID)
With this invaluable information in hand, the security team gains the upper hand, conveniently identifying:
- Identities accessing the cloud service from an extensive array of unique geolocations
- Identities engaging with the cloud service through a wide range of distinct applications
Now, let us move from theory to practice.
To generate a list of identities that have accessed Azure AD and their unique geo-location within the past 90 days, execute the following command:
./ual_tool.ps1 -ops ADLogin -analyze IP -days 90The following output shows an actual result with an identity that has accessed Azure AD from over 3 unique geo-locations.
"ACCOUT_1": {
"Unique IP Count": 3,
"Unique Countries Count": 3,
"IP Properties": {
"IP RETRACTED": {
"Count": 3,
"Country": "SINGAPORE"
},
"IP RETRACTED": {
"Count": 29,
"Country": "MALAYSIA"
},
"IP RETRACTED": {
"Count": 29,
"Country": "INDONESIA"
}
}
}
To generate a list of identities that have accessed Azure AD and their unique application accessed within the last 90 days, execute the following command:
./ual_tool.ps1 -ops ADLogin -analyze AppID -days 90And the following output shows an actual result with an identity that has accessed Azure AD from over 7 unique application types.
"ACCOUNT_2": {
"Unique Count": 7,
"AppID Properties": {
"4765445b-32c6-49b0-83e6-1d93765276ca": {
"Name": "OfficeHome",
"Count": 3
},
"89bee1f7-5e6e-4d8a-9f3d-ecd601259da7": {
"Name": "Office365 Shell WCSS-Client",
"Count": 18
},
"7eadcef8-456d-4611-9480-4fff72b8b9e2": {
"Count": 1,
"Name": "Unknown"
},
"c9a559d2-7aab-4f13-a6ed-e7e9c52aec87": {
"Name": "Microsoft Forms",
"Count": 2
},
"fb78d390-0c51-40cd-8e17-fdbfab77341b": {
"Name": "Microsoft Exchange REST API Based PowerShell",
"Count": 4
},
"243c63a3-247d-41c5-9d83-7788c43f1c43": {
"Name": "Office Online Core SSO",
"Count": 2
},
"00000003-0000-0ff1-ce00-000000000000": {
"Name": "SharePoint Online",
"Count": 2
}
}
}
The results can be sorted further based on the value of ‘Unique Count’. This will help analysts in identifying the identity with the most unusual access pattern.
The table below lays out an array of ‘ops‘ parameters, serving as a guide for analysts seeking to uncover anomalies across numerous services:
| Parameter options | Services |
| ADLogin | Azure AD |
| OD_Access | OneDrive |
| SP_Access | SharePoint |
| EXO_Access | Exchange |
In the CASUAL PowerShell script, you can find the mapping of operations to the parameters. And since Microsoft has pledged to expose more audit log types which are previously available only to organizations with the E5 licenses, the tool will be able to provide more visibility soon.
As you navigate through the intricacies of digital security, CASUAL can be an invaluable tool, streamlining your quest to find compromised identities. We hope that this tool empowers you and facilitates a smoother and more effective pursuit of cybersecurity excellence.
Limitations of CASUAL
- Unusual Application types are not automatically identified
CASUAL simply generates a list of identities discovered in the UAL and the AppIDs used by those identities. An AppID that may be considered unusual for one identity may be normal for another. For example, an account belonging to a security team member might be expected to use PowerShell to access the cloud services, but this could be unusual for someone in the finance team. It is important to apply proper context when analyzing the results. One way is to start building a baseline with the data generated by the tool. - Geo-location information may be inaccurate
The geo-location could be misreported by the IP lookup service, or unresolvable due to the lookup cap enforced. If the tool reports an identity accessing the cloud service from an unexpected geolocation, verify the location by checking the IP with a reputation lookup service.
CSX – Simplifies cloud security
Unlike CASUAL, CSX (Cloud Security X) is designed to overcome the limitations mentioned above, making it an essential subscription for any organization serious about its cybersecurity posture.
CSX is an innovative solution that makes comprehensive and easy-to-use cloud security available. Leveraging innovative analytics and AI, CSX enables strong security across all layers of the cloud, covering IaaS, PaaS, and SaaS. CSX was also a project awarded by the Cyber Security Agency (CSA) of Singapore on CSA’s Cybersecurity Innovation Day 2022.
CSX reduces the personnel burden in cybersecurity. It saves costs for businesses while providing strong cloud security.
By subscribing to CSX, you are equipping your organization with cutting-edge technology that leverages AI, advanced analytics, and contextual awareness to provide a higher level of security intelligence. Embrace the limitless potential of CSX to safeguard your cloud assets and maintain a strong defense against ever-evolving cyber threats.





