InsiderSecurity conducts in-depth research and analysis on emerging cyber threats, so as to equip organizations with the knowledge to proactively protect themselves. In light of recent events, our Insider Lab team has thoroughly examined the methods and exploitation techniques employed by the notorious Volt Typhoon Attacks. Furthermore, we delved into the early detection strategies and practical measures to counter these threats. Here are the key findings from our investigation:
Volt Typhoon attacks
On May 24, 2023, Microsoft and the “Five Eyes Alliance” cybersecurity information sharing organization released a joint cybersecurity advisory, which detailed a series of activities related to the Volt Typhoon. According to Microsoft’s blog post, these malicious activities have been ongoing since mid-2021 and have targeted critical infrastructure sectors in Guam and the United States. The sectors affected include communication, manufacturing, utilities, transportation, construction, maritime, government, IT, and education.
What sets these attackers apart is their extensive utilization of Living-off-the-land techniques (LOLT), which prioritize stealth and obfuscation. Remarkably, the attackers refrained from introducing any discernible malware, custom code, or binaries into the compromised systems. By doing so, they successfully evaded antivirus and endpoint detection and response (EDR) solutions, enabling them to freely navigate the networks and systems.
In this article, Insider Lab provides valuable insights into detecting such stealthy attackers throughout the various stages of an attack. We focus on the utilization of User and Entity Behavior Analytics (UEBA), a behavioural-based security solution designed specifically to identify threats posed by these lurking attackers within the network.
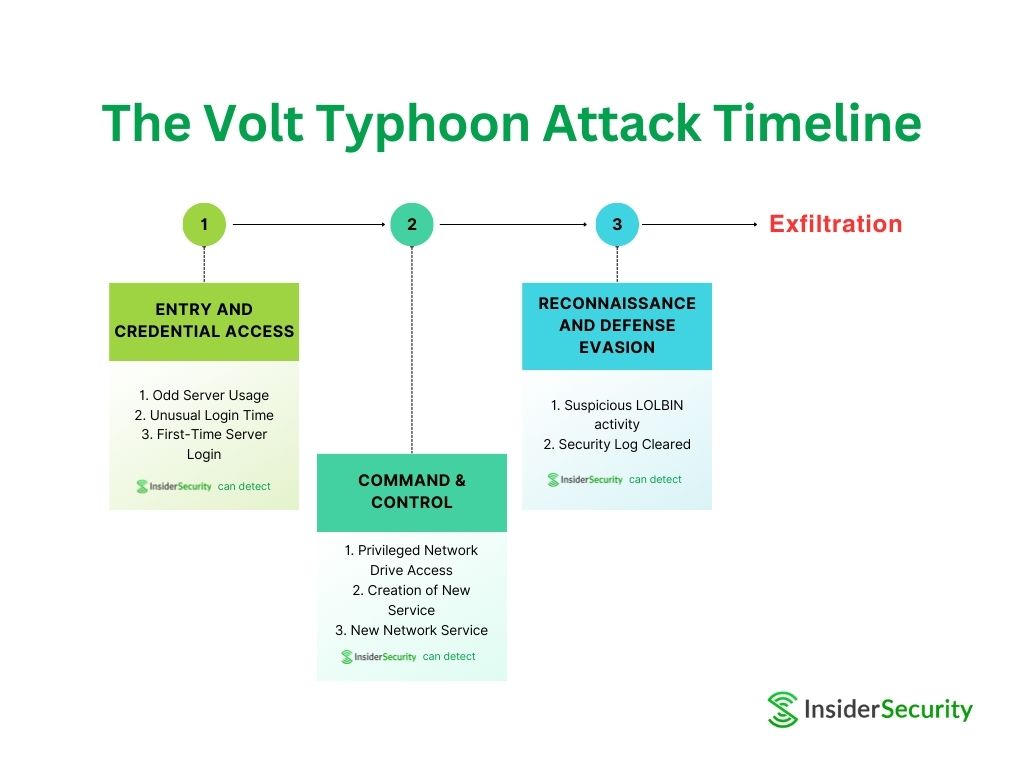
Stage 1: Entry and credential access
During the initial phase of the attack, the intruder managed to gain entry into the enterprise’s intranet by initially infiltrating the router’s management interface (step 1).
| Note: While it is uncommon for the management interface to be exposed directly to the internet, this may be necessary if the device is managed by a third party. |
Subsequently, they discovered credentials stored within the router, allowing them to access the network’s assets (step 2).
To illustrate this stage, let’s consider a scenario where the attacker stumbled on the credential ‘RouterAdmin1’ stored within the router and utilized it to gain access to the domain servers present within the enterprise’s network.
| Note: The rationale to store access credentials (to other network assets) within the router is unclear. However, this might be necessary if specific capabilities of the router have been activated. One such example is when the router needs to retrieve specific records from the identity management server, which is typically the Domain controller. |
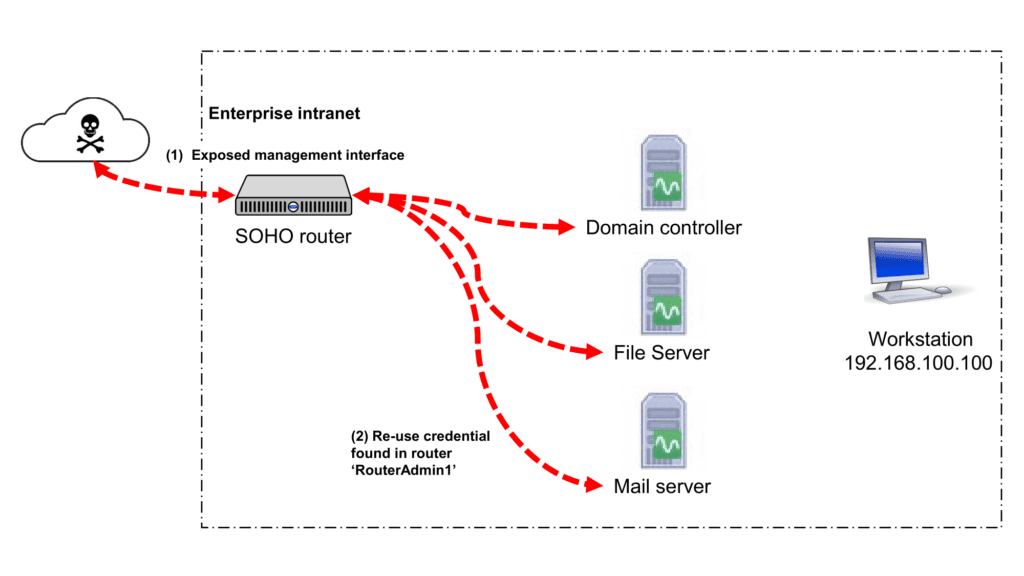
To detect steps (1) and (2) effectively, behavioural-based algorithms can be leveraged. By monitoring deviations in login behaviour, the following three use cases can trigger alerts when the ‘RouterAdmin1’ account is misused:
- Odd Server Usage
- Unusual Login Time
- First-Time Server Login
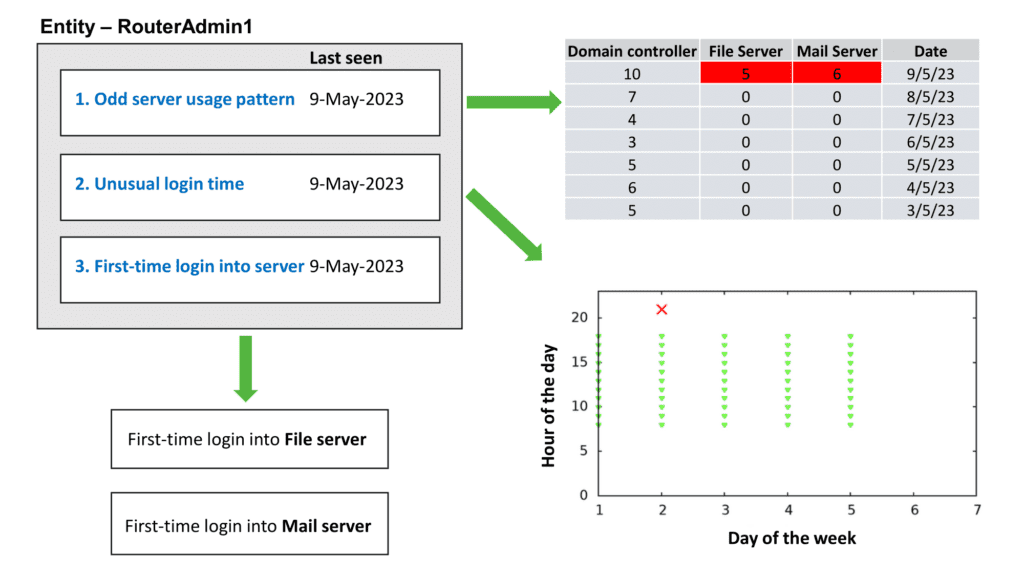

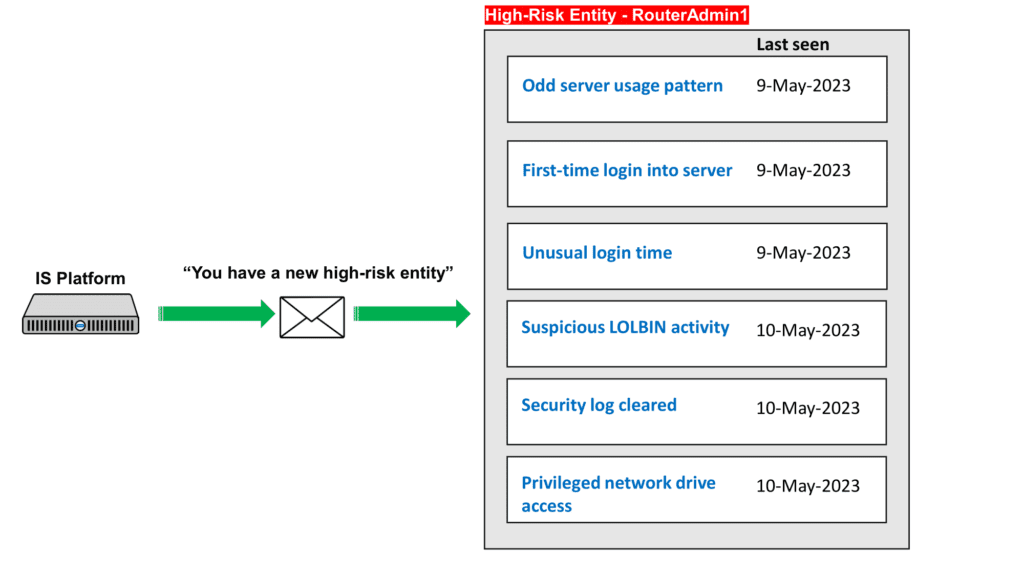
In the ‘Odd server usage’ use case, advanced behavioural analysis can detect anomalies in the usage patterns of the ‘RouterAdmin1’ account. In the event of lateral movement, if the ‘RouterAdmin1’ account is being used to access servers in a way that deviates significantly from a user’s previous patterns, an anomaly alert will be generated. For example, if an attacker gains access to the ‘File server’ and ‘Mail server’ by utilizing the ‘RouterAdmin1’ account instead of the authorized user’s account, this would trigger an alert.
In the ‘First-time login into server’ use case, an anomaly alert will be promptly triggered when the account logs into the server for the first time.
In the ‘Unusual login time’ use case, an anomaly alert will be generated when the account logs into the server at a time that significantly deviates from its established login timing.
The convergence of these anomalies will increase the risk score associated with the ‘RouterAdmin1’ entity, strongly indicating malicious activities.
Stage 2: Command & Control
During stage 2 of the attack, the attacker utilizes the PSEXEC to execute commands on a remote server. PSEXEC.EXE, a Microsoft tool, enables privileged users to launch processes on a remote server. Based on the NSA’s document the attacker launches the NETSH.EXE command on the File server using PSEXEC.EXE in the Domain controller (step 3).
| C:\pstools\psexec.exe” \\{REDACTED} -s cmd /c “cmd.exe /c “netsh interface portproxy delete v4tov4 listenaddress=0.0.0.0 listenport=9999” |
The attacker was also observed executing the following command to establish a network connection tunnel.
| netsh interface portproxy add v4tov4 listenaddress=0.0.0.0 listenport=9999 connectaddress={REDACTED} connectport=8443 protocol=tcp |
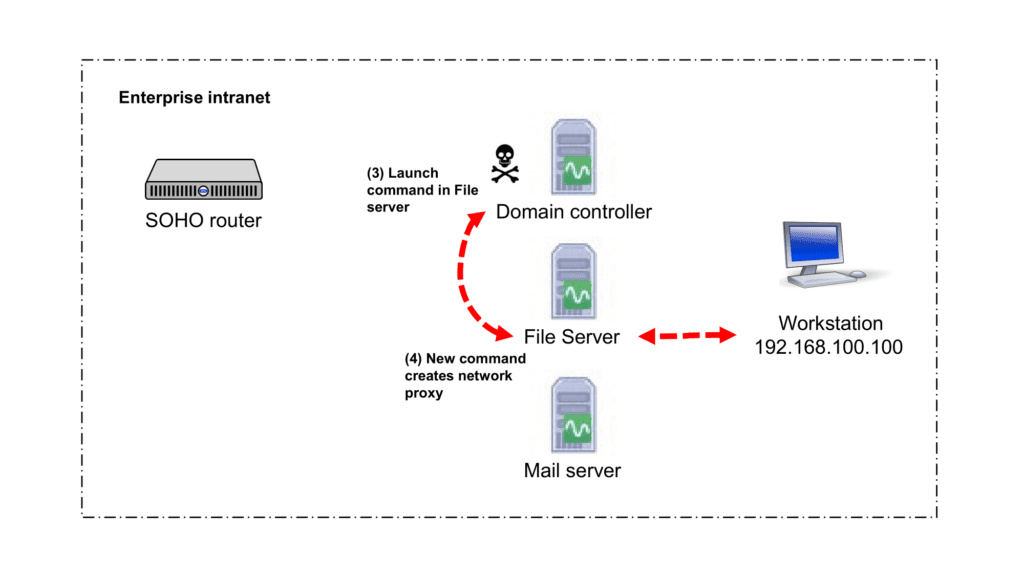

To effectively detect steps 3 and 4, which involve the execution of privileged actions, the following use cases can be leveraged:
- Privileged Network Drive Access
- Creation of New Service
- New Network Service
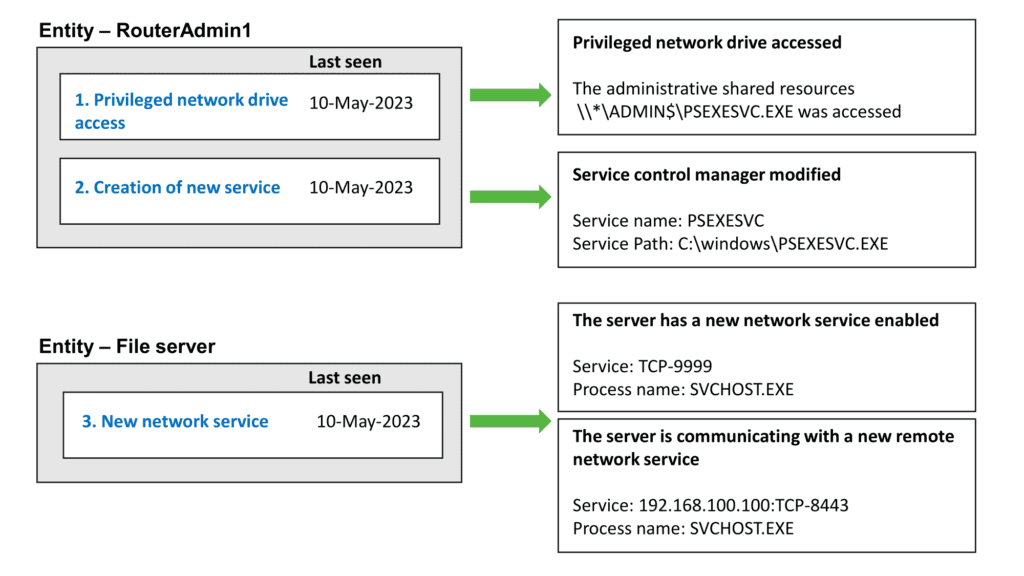

In the use case of privileged network drive access, an anomaly alert will be triggered when the account accesses a privileged drive such as \\SERVER\ADMIN$. This hidden drive exists in Windows servers and enables privileged users to access the \Windows\ folder of the server. The \SERVER\ADMIN$ drive is commonly utilized by tools like PSEXEC to upload binaries into the server.
In the use case of creating a new service, an anomaly alert will be promptly generated when a new system service is created. A specific example of concern is the PSEXEC tool, which creates and launches PSEXESVC.EXE as a new system service after successfully uploading the binary.
In the use case of a new network service, an anomaly alert will be triggered upon the detection of new network connectivity or services. Specifically, this includes instances where NETSH.EXE is utilized to establish a network proxy that listens on TCP port 9999. Moreover, the network proxy is configured to forward incoming data to TCP port 8443 at the IP address 192.168.100.100.
The presence of the new network service listening on TCP port 9999, as well as the outgoing connection to 192.168.100.100 on TCP port 8443 can be identified by the network anomaly algorithm.
Stage 3: Reconnaissance and defense evasion
In stage 3 of the attack, the attacker executed a sequence of natively available commands to gather additional information (Step 5). These commands provide various information, including network settings, account details, running processes, and more. Finally, they attempted to clear the security log in order to conceal their tracks (Step 6).
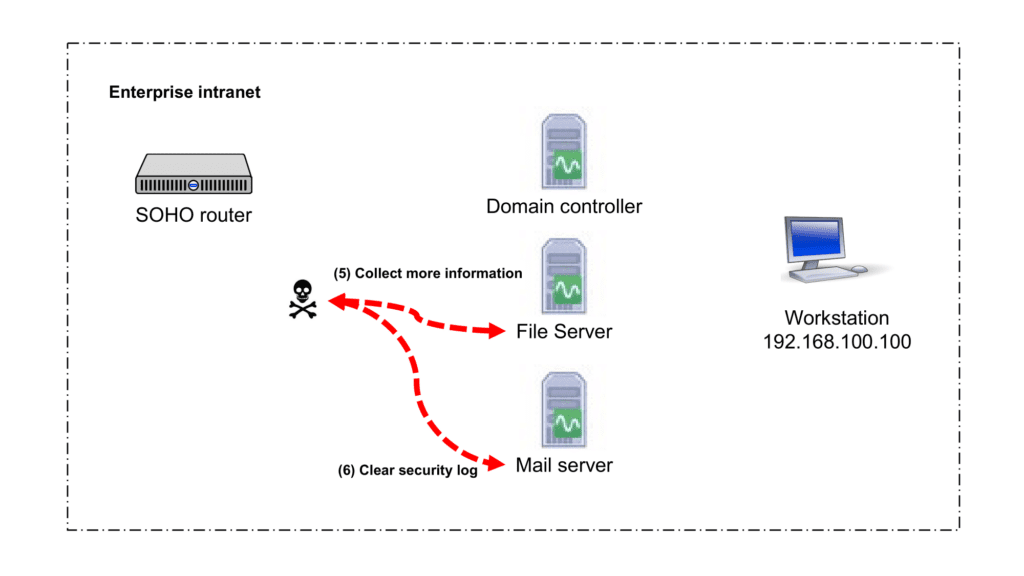

To detect steps 5 and 6 effectively, the following use cases can be leveraged:
- Suspicious LOLBIN activity
- Security Log Cleared
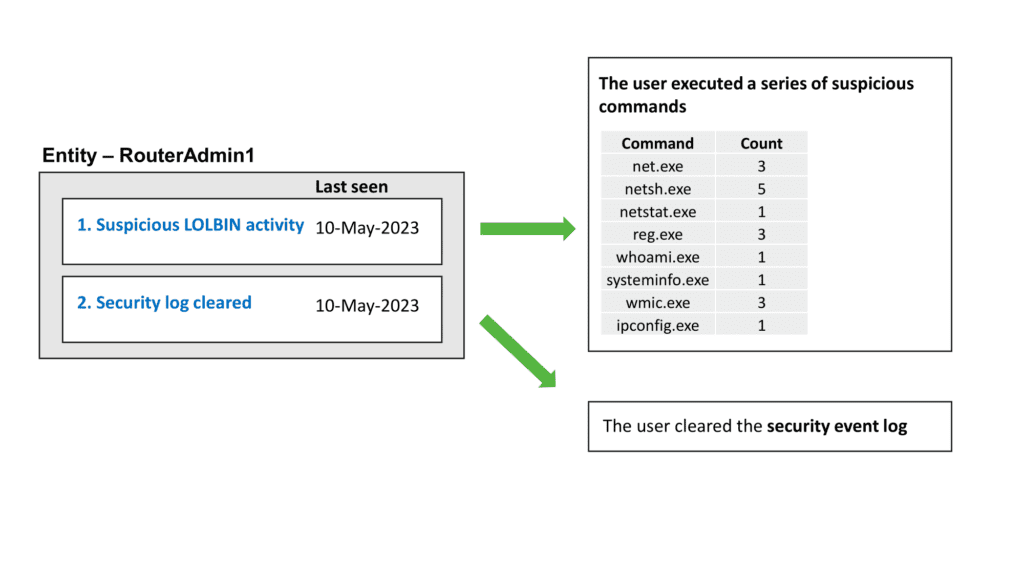

In the use case of suspicious LOLBin (Living-off-the-Land Binary) activity, an anomaly alert will be generated when a series of native commands are executed in a pattern that closely resembles the activities typically carried out by an attacker during reconnaissance and maintaining access.
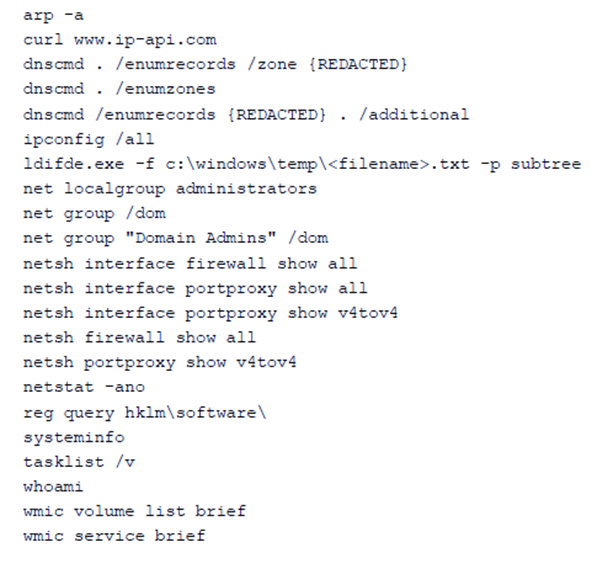
These are the specific LOLBin commands outlined in the advisory released by the NSA pertaining to the campaign:

In the use case of security log clearance, an anomaly alert will be triggered when the account attempts to clear the security event log. This deliberate action poses a significant concern as it obstructs forensic analysis and investigation, especially when the victim lacks access to the audit trail.
This underscores the importance of forwarding the audit log to a secure and resilient log storage facility to preserve crucial evidence for future analysis.
Auto triage of security alerts
In the previous sections, we discussed the use cases for detecting stealthy attackers in a network. While one can try to use a SIEM (Security Information and Event Management) solution to implement some of these use cases, there are significant limitations to consider when using a SIEM solution for such use cases.
For example, monitoring Event ID 1102 can help detect the clearing of security logs, while Event ID 5145 can identify privileged network drive access. However, enabling these alerts in a SIEM may overwhelm the security team with numerous alerts, including many that are benign or unrelated to malicious activity.
To address this challenge, UEBA (User and Entity Behavior Analytics) will be an effective approach. UEBA continuously triages and compares activity against the historical behavioural of entities. The security team is only notified when behavioural changes linked to relevant use cases are detected, minimizing alert fatigue.
By leveraging UEBA, security alerts are analyzed in the context of an entity’s overall behaviour, allowing for a more accurate and targeted detection of suspicious activities. This approach significantly reduces the number of false positives and focuses attention on the most relevant alerts, improving the efficiency and effectiveness of the security team’s response to potential threats.

Summary and recommendations
The attacker’s patient execution of the campaign, relying on the operating system’s limited tools and living-off-the-land (LOL) techniques, emphasizes the need for proactive security measures. To safeguard your organization against such threats, we recommend implementing the following measures:
- Restrict direct internet access to the router’s management interface
- Maintain credentials stored in the router at lower privilege levels
- Implement comprehensive authentication and authorization measures for both intranet and internet-facing assets
- Establish a secure and centralized location for forwarding and storing audit logs
- Take a proactive approach by continuously monitoring audit logs for any abnormalities related to identity, network, and assets. Detecting anomalies early can help mitigate potential threats before they escalate
How can InsiderSecurity help?

InsiderSecurity’s Automated UEBA (User and Entity Behavior Analytics) powered by AI and advanced user behaviour analytics provides early detection of various security risks, including hijacked accounts, insider threats, and compromised servers. By leveraging our Automated UEBA, organizations can effectively detect all the above-mentioned attack pathways.
Through continuous monitoring and analysis of user behaviour, InsiderSecurity identifies suspicious activities, anomalous patterns, and deviations from normal behaviour. This allows for the proactive identification of potential security incidents and timely response to mitigate risks.
InsiderSecurity’s Automated UEBA goes beyond traditional rule-based approaches, utilizing advanced machine learning algorithms to detect complex and evolving attack techniques. By analyzing user behaviour, account activity, network traffic, and other relevant data sources, our solution provides enhanced visibility into potential threats and helps organizations stay one step ahead of adversaries.
Elevate your security posture and protect your organization from sophisticated threats. Contact us now to schedule a consultation and discover how our advanced security solutions can help you stay ahead of evolving cyber risks. Don’t wait until it’s too late – act now to secure your future.





