Understanding the LastPass hack
This marks the initiation of a series exploring hacks spotlighted in CSA’s renowned paper on the Top Threats to Cloud Computing. Delving into the LastPass hack, this article aims to offer an easy-to-read, illustrated guide. Additionally, we will provide guidelines for detection.
LastPass, a Software as a Service (SaaS) provider, offers a password vault service. These services are typically used for the secure storage of secrets and are popular with security-conscious individuals, as they facilitate the secure and easy storage of complex passwords.
LastPass assures customers that they do not have knowledge of the actual secret stored in their system because of LastPass’s zero-knowledge architecture, which includes the following:
- Data is stored encrypted in LastPass’s database.
- The encrypted data can only be decrypted with the master password provided by the customer just-in-time.
- The master password provided by the customer is never stored in any persistent storage in LastPass’s system.
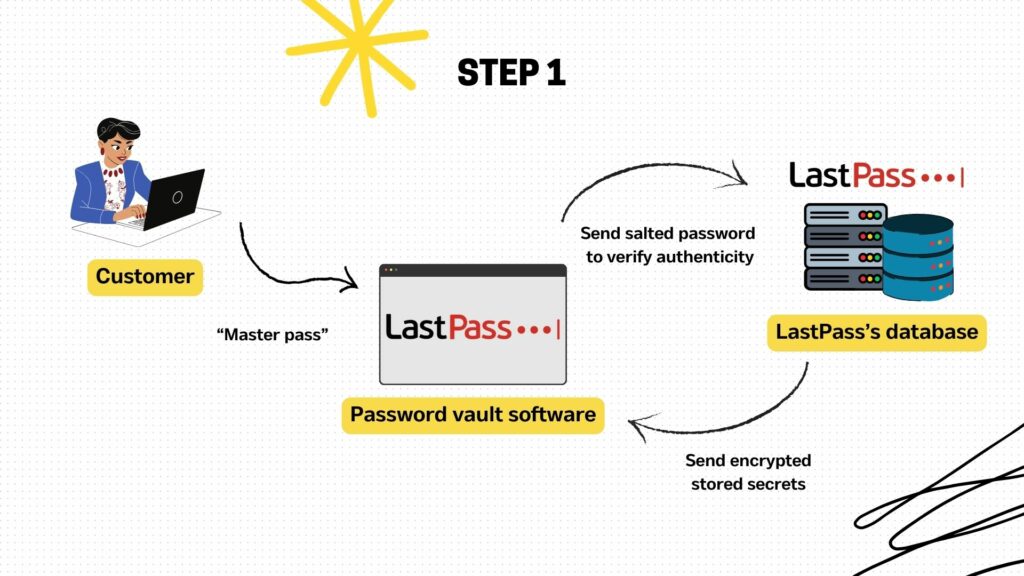
The following diagrams help illustrate how such a password vault works.
Step 1: The customer launches the password vault software and provides the master password. The master password might be salted or hashed further to ensure secrecy in transit before it is sent to the password vault’s server for authentication. Upon successful authentication, the password vault server sends the encrypted secrets to the customer.
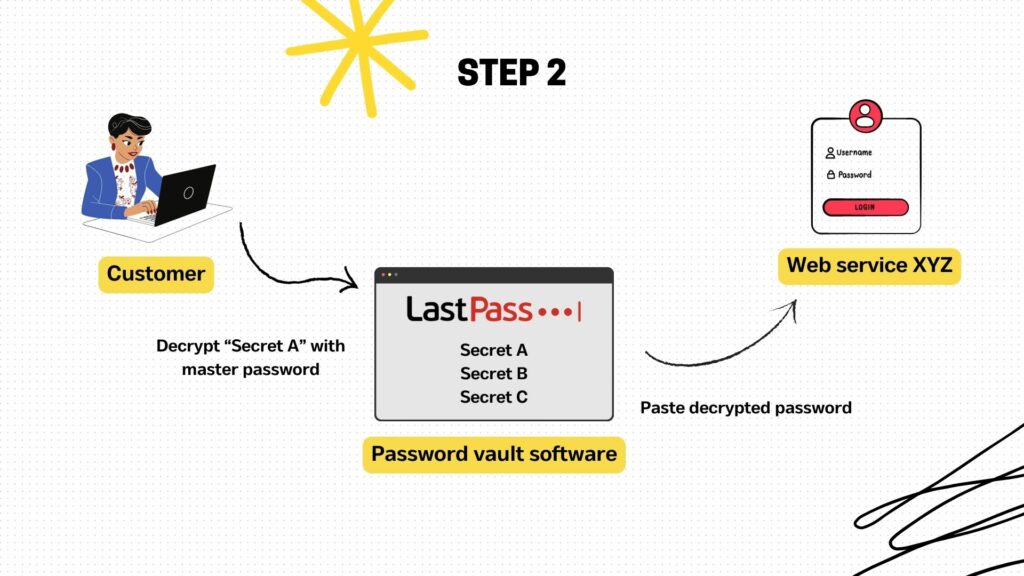
Step 2: The customer can now decrypt the encrypted secrets with the master password. These secrets can typically be copied into the clipboard for Just-in-time usage. In the illustration, the customer has decrypted and copied the ‘Secret A’ into the Clipboard. The customer can now login to another software or web portal which requires Secret A to access.

In the incident of LastPass hack, the customer’s encrypted password (X), as shown in the illustration, was stolen. Additionally, customer information, such as the company name and the URL where the decrypted password could be used, was also compromised.
One can imagine the impact this could have had on the industry if the attacker had been able to decrypt any password they had stolen. This would mean the attacker could access any password-protected systems easily accessible from the internet. Of course, this is only applicable if 2FA is not present in those accounts!
The LastPass hack unveiled
How possible is it to decrypt the secrets stolen from LastPass?
Since the secrets are stored encrypted, what are the possibilities that the attacker could recover the secrets? There are multiple ways these encrypted passwords can be decrypted, and we will be discussing two possible methods:
- Password guessing:
As the secrets are stored encrypted with the customer’s master password, if a weak master password has been used, the attacker can easily guess the customer’s master password to access the data and reveal all the passwords stored by the customer.
- Tampering with the backend code:
If the attacker compromises the backend server responsible for decrypting the encrypted data and plants malicious code, they could potentially log the customer’s master password and use it to decrypt the stolen data.
How the Attack Happened
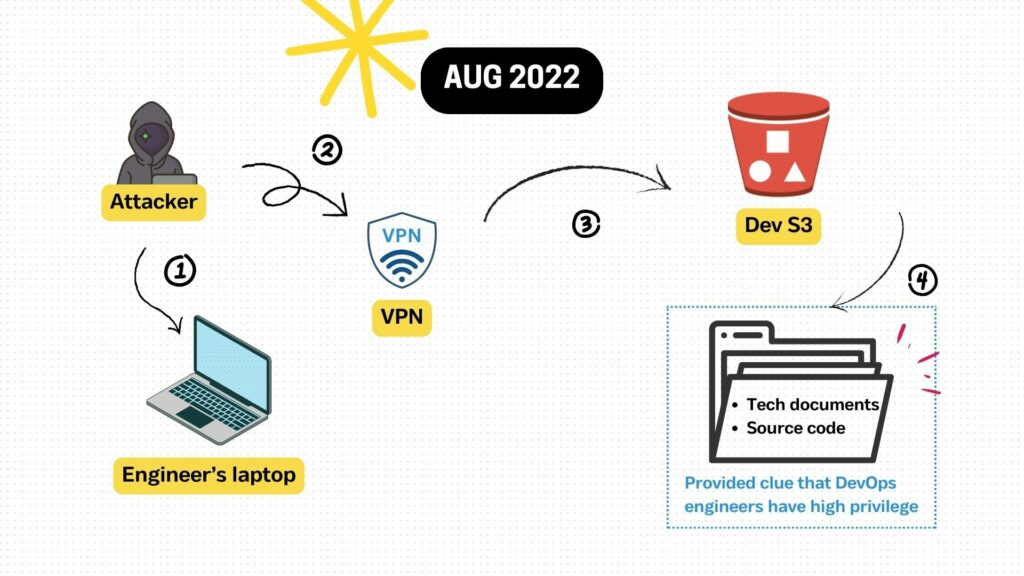

In early August 2022, attackers successfully accessed LastPass’s S3 bucket in a development environment and exfiltrated source code together with technical documents (4). A developer’s valid credentials, stolen from the developer’s compromised machine (1), were used to access the S3 bucket (3). It is interesting to note that the developer does not usually access those resources on S3; however, the access given to the developer has been overly permissive. It is also noted that the attackers obfuscated their original location by accessing the cloud resource over VPN (2).
In mid-August 2022, the LastPass security team discovered the hack and decommissioned the development environment, under the assumption that the attacker’s activity had been contained.
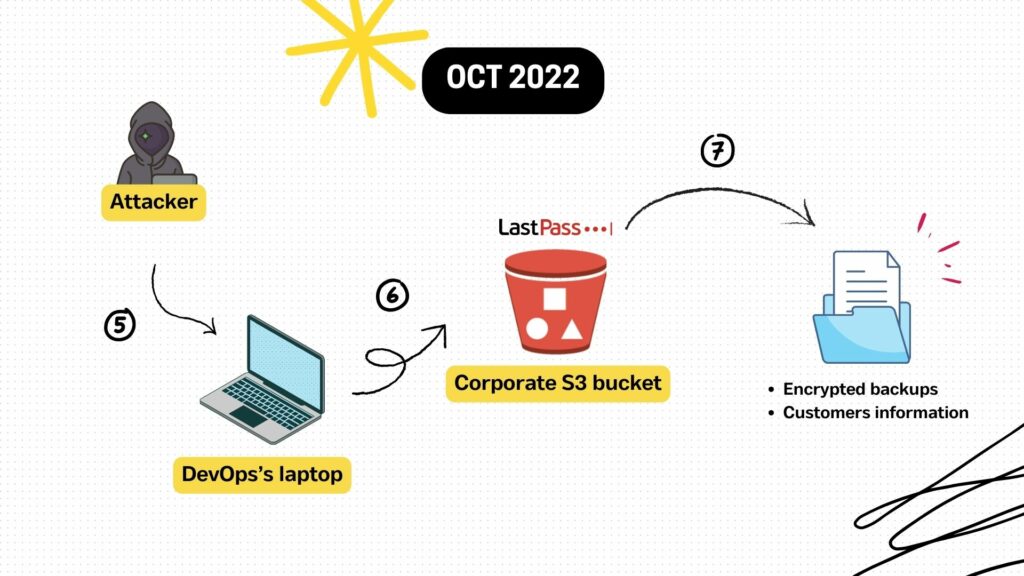

In October 2022, a LastPass Senior DevOps engineer’s machine was compromised (5) and used to access the DevOps engineer’s LastPass corporate vault. This allowed the attacker to access the corporate vault in the S3 bucket (6), which contains backups of LastPass customer data and encrypted vault data. Fortunately, the customers’ secrets remain safe as they are encrypted in the customer’s master key due to the zero-knowledge architecture.
LastPass discovered the hacks after the attackers triggered an ‘IAM unauthorized activity’ alert generated by AWS GuardDuty, likely be caused by running reconnaissance and enumeration operations (4).
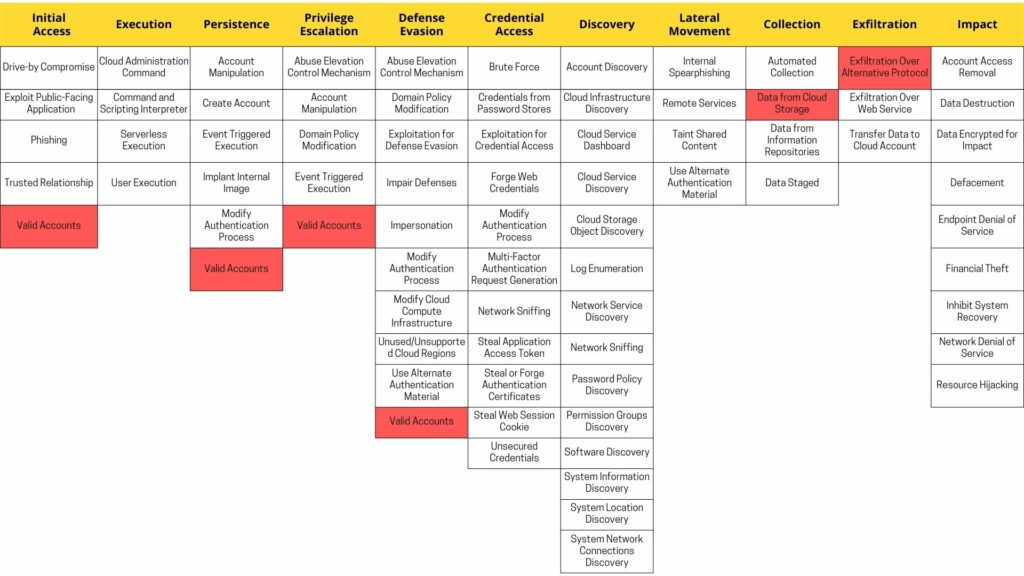
We can map the attacks to the following Tactics, Techniques, and Procedures (TTPs) in MITRE.

Detection and prevention strategies
There are multiple opportunities for detection. Let’s walk through the timeline and determine possible detection strategies.
In (2) and (3), when the attacker was accessing the cloud resource over VPN, we can detect such activities by:
- Detecting logins from unusual locations or fast-flux location changes.
- Detecting logins from VPN IP ranges.
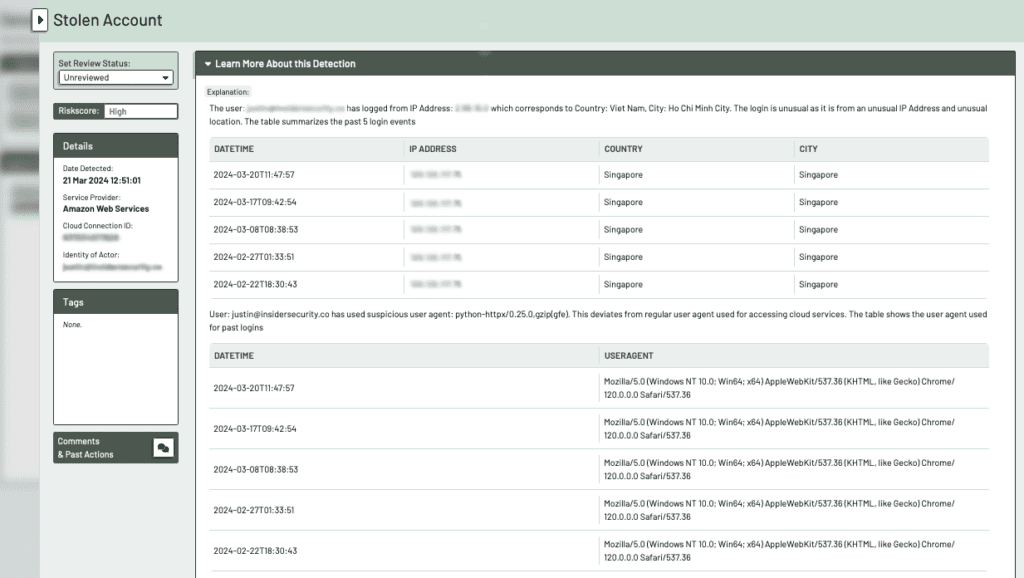

Storage locations with sensitive data should be tagged, and accessing such data should be monitored. In (4) and (7), when the attacker was accessing sensitive data, we could trigger an alarm.
In (6), when the attacker exfiltrated a hoard of data from the S3 buckets, we can detect this by monitoring for an unusually high intensity in data access. Since the accounts do not usually access that data, this form of alerting will have very low false positives.
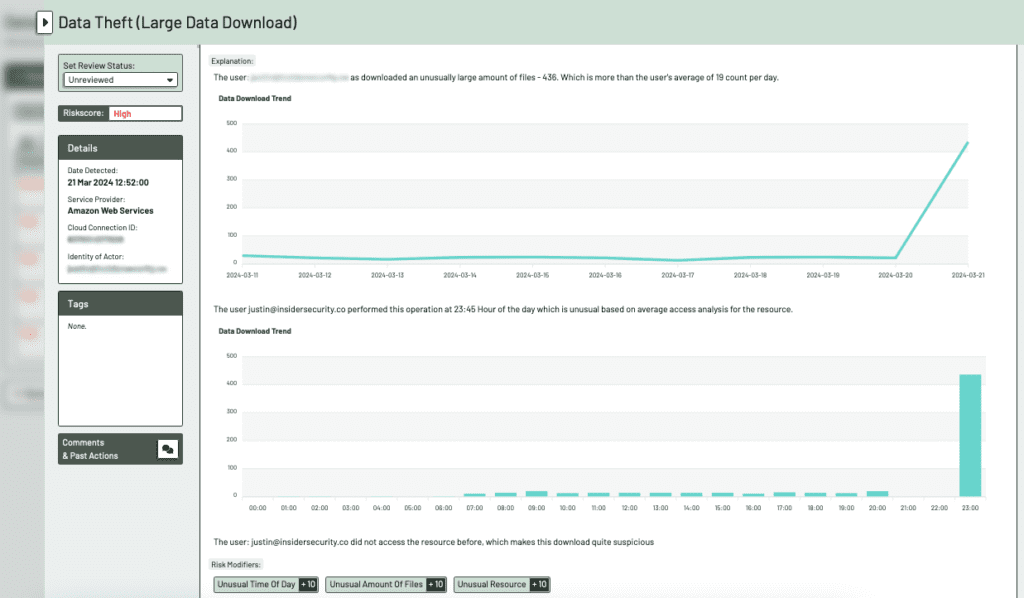

Finally, when the attackers are performing reconnaissance and enumeration, they tend to execute a number of privileged activities to verify the privileges of the compromised account. These can be detected by comparing the usual privileged activities the authentic account would perform with those executed by the attacker.
Staying ahead of cyber threats
Innovative solutions by InsiderSecurity
Looking for ways to stay ahead of any cyber threats? InsiderSecurity provides advanced cybersecurity behavior analytics products that help your company to uncover cyber threats before there is any serious data loss. We offer a range of solutions, including Automated UEBA for securing on-premise and cloud IT infrastructure, as well as the CSX for ensuring cloud data security.
CSX is designed to detect sophisticated attacks described in this article making it an essential subscription for any organization serious about its cybersecurity posture. Beyond detecting threats, CSX offers recommendations and a user-friendly avenue for executing remedial actions and implementing mitigation strategies.