Cloud Security Monitor
Detect malicious user activity
in Microsoft 365 early
Securing Microsoft 365
Cloud Security Monitor is a simple-to-use SaaS for enterprises to monitor their data security in Microsoft 365. Discover the internal threat very early, before there is any serious data loss.
With its award-winning automated cybersecurity analytics and machine-learning, Cloud Security Monitor makes sense of the high volume of Microsoft 365 activity events, so that you do not have to. Finally, an easy way to monitor your Microsoft 365 data security.
With its award-winning automated cybersecurity analytics and machine-learning, Cloud Security Monitor makes sense of the high volume of Microsoft 365 activity events, so that you do not have to. Finally, an easy way to monitor your Microsoft 365 data security.
Monitor for compromised Microsoft 365 accounts
Discover if any of your Microsoft 365 accounts are compromised and whether a hacker is accessing your company data and emails.


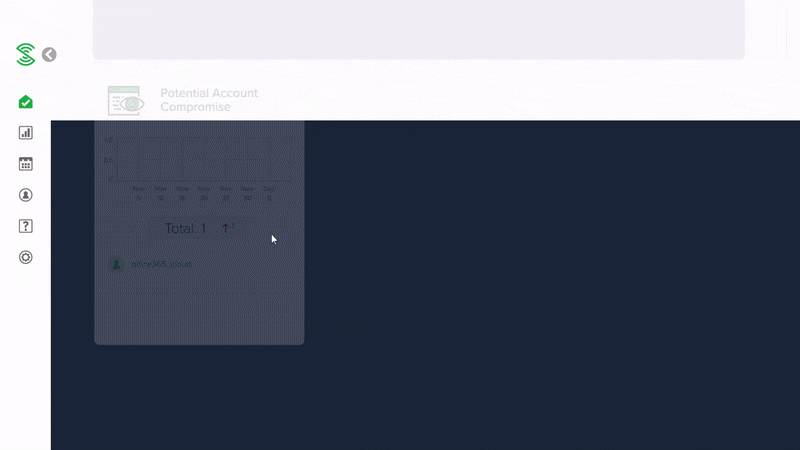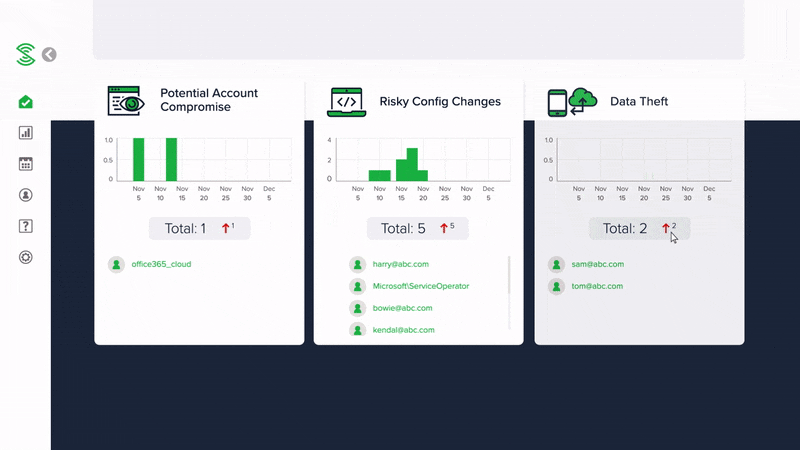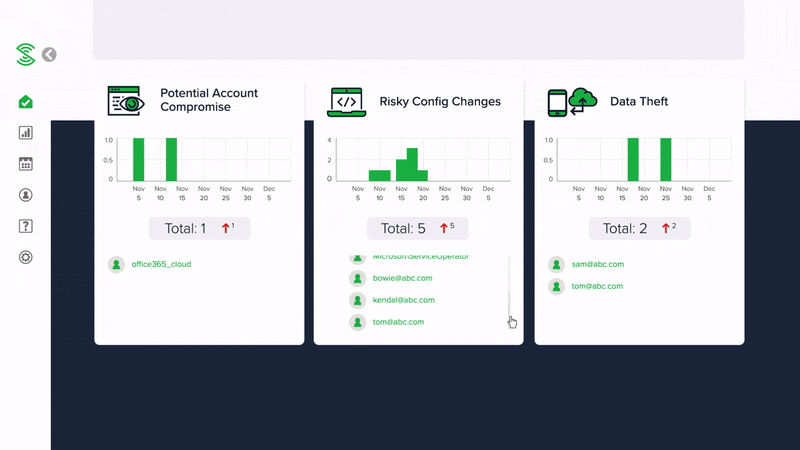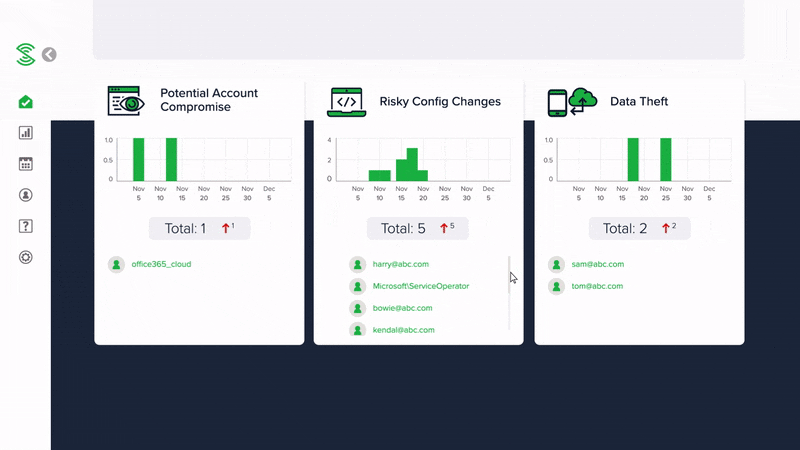

Monitor for insider threats and suspicious data access
Discover if there is a insider threat or hacker stealing valuable company data from Sharepoint or OneDrive
Monitor for documents shared to public by accident
Smart algorithms automatically discover if your files are accidentally left exposed.
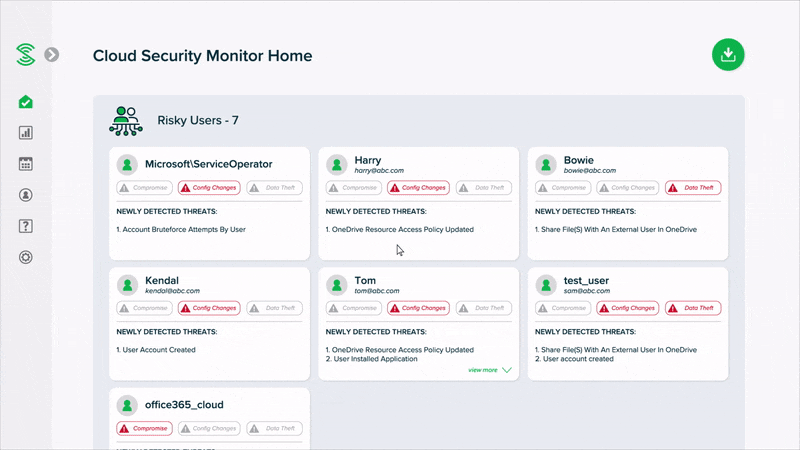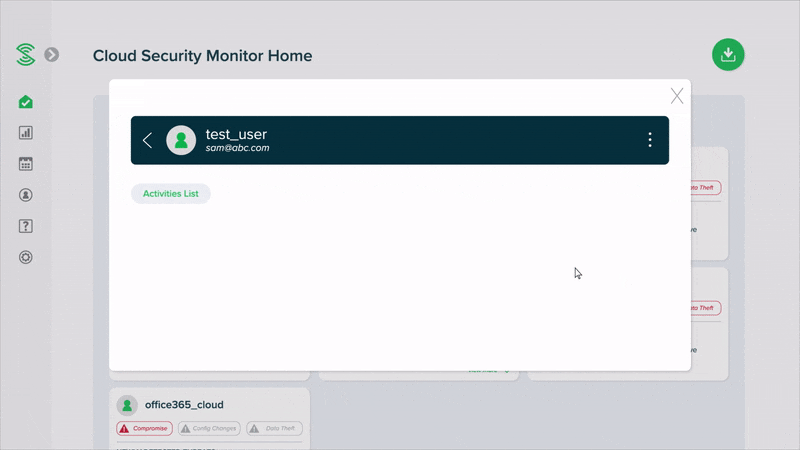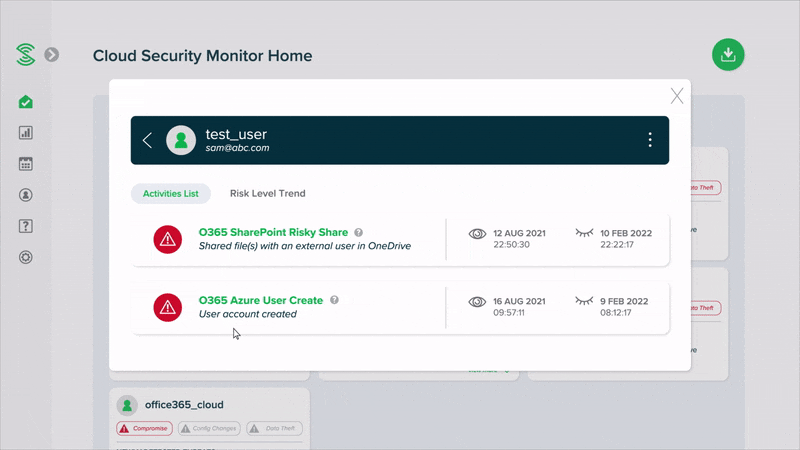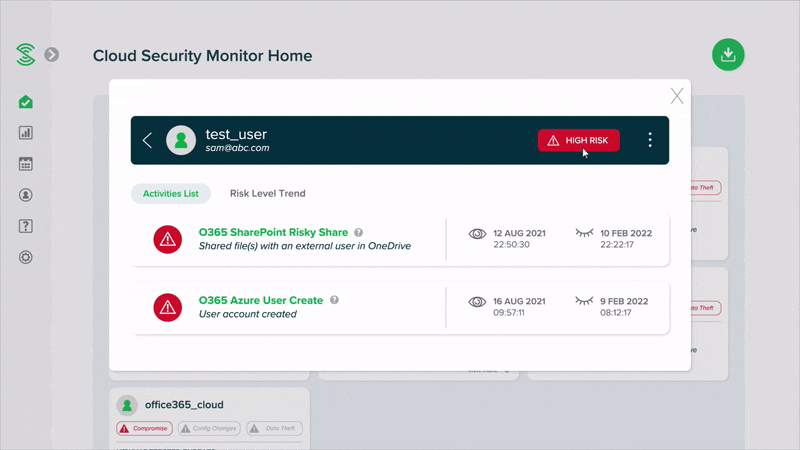

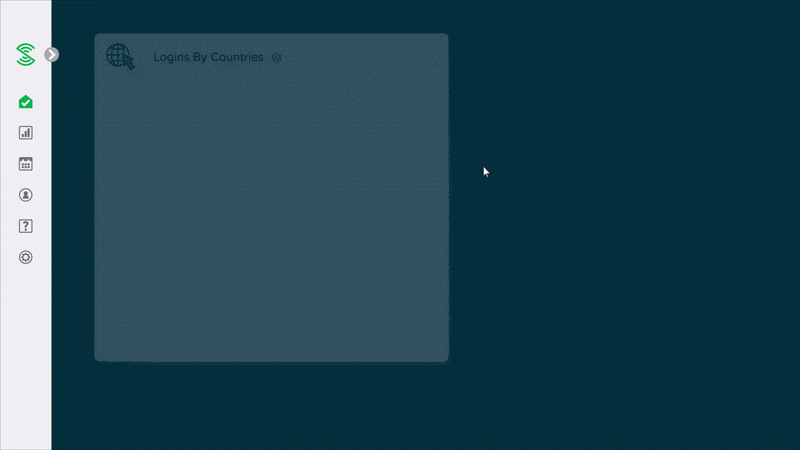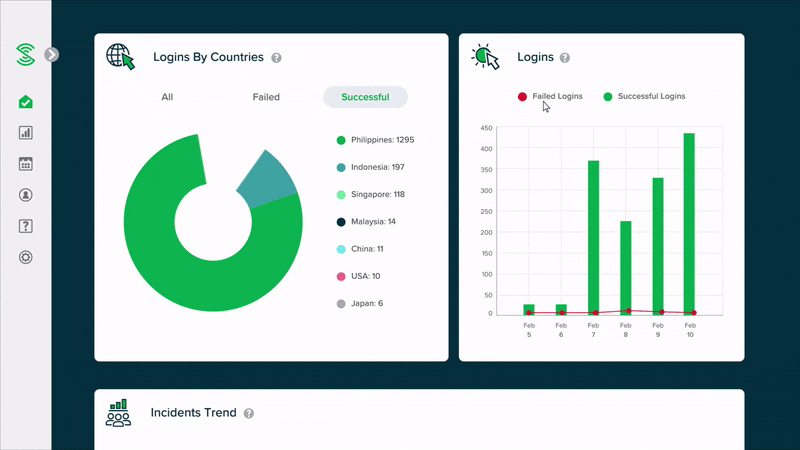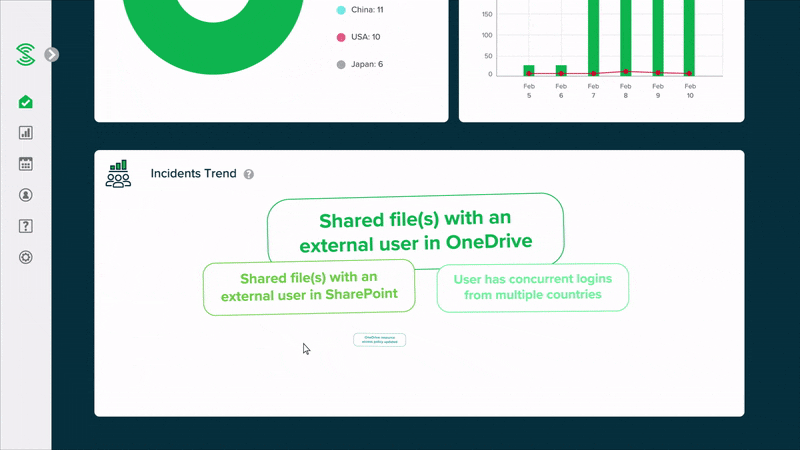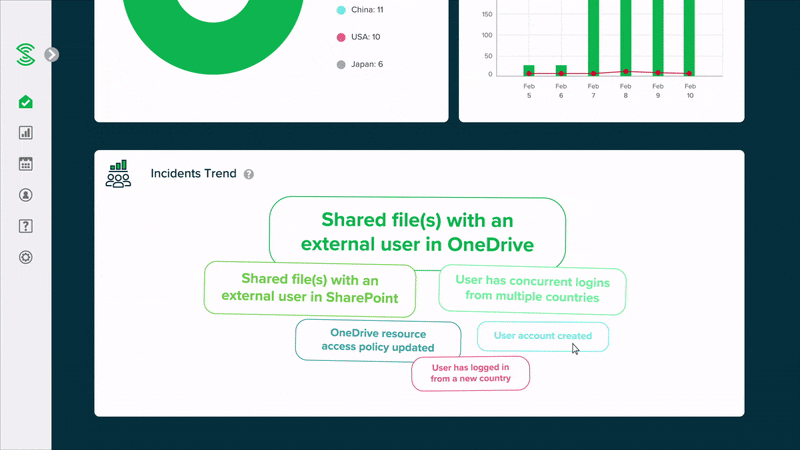

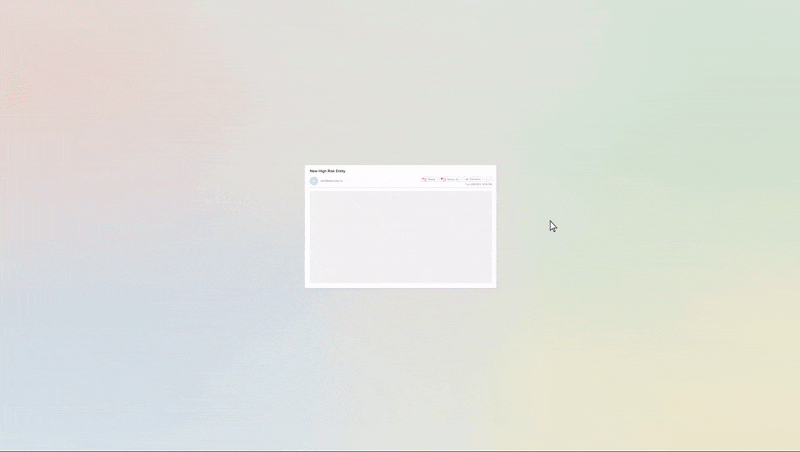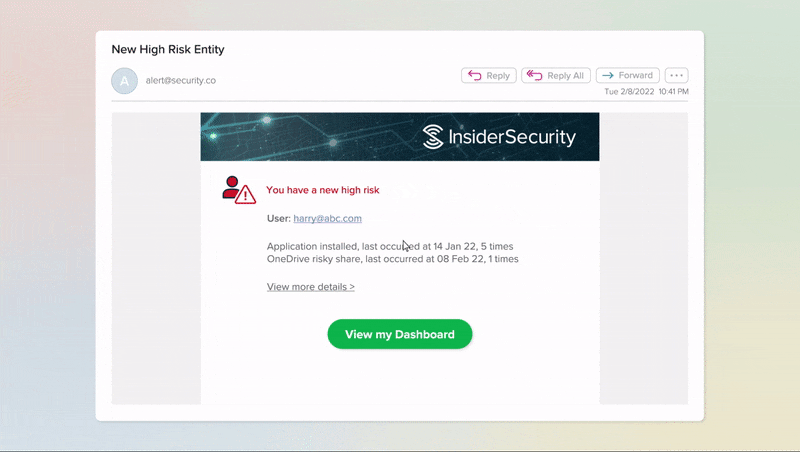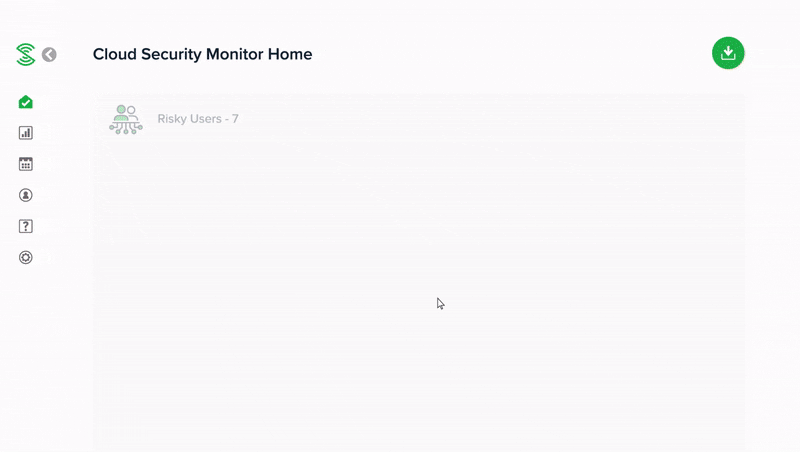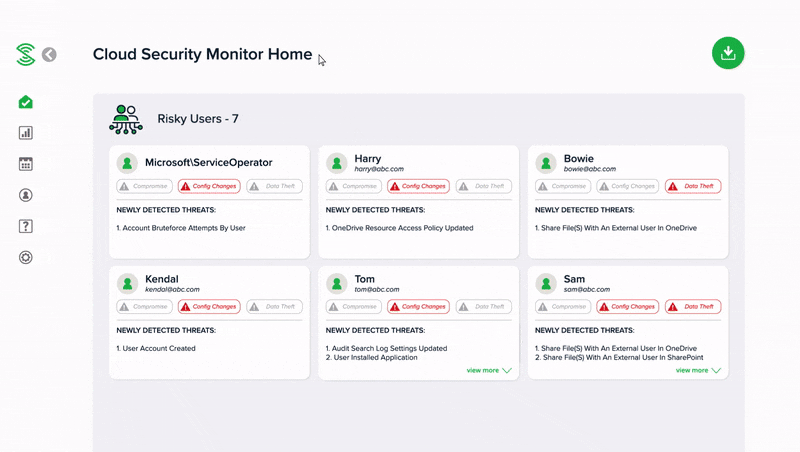
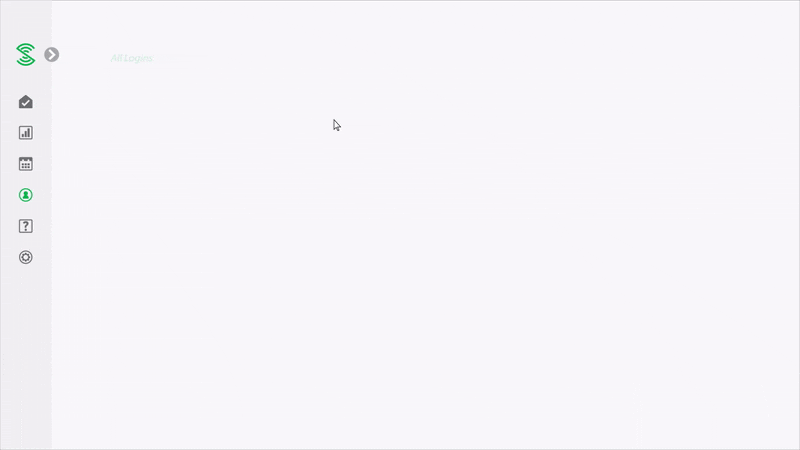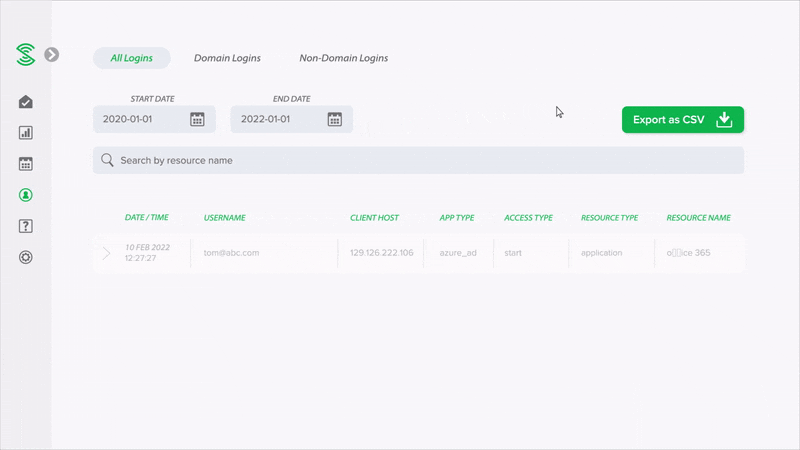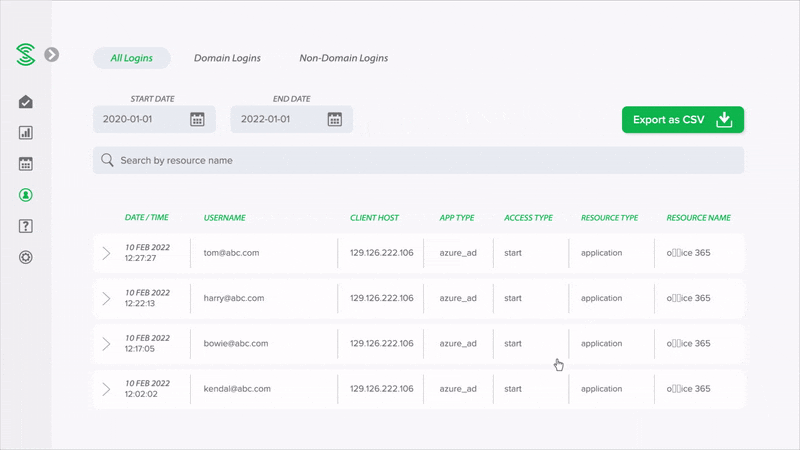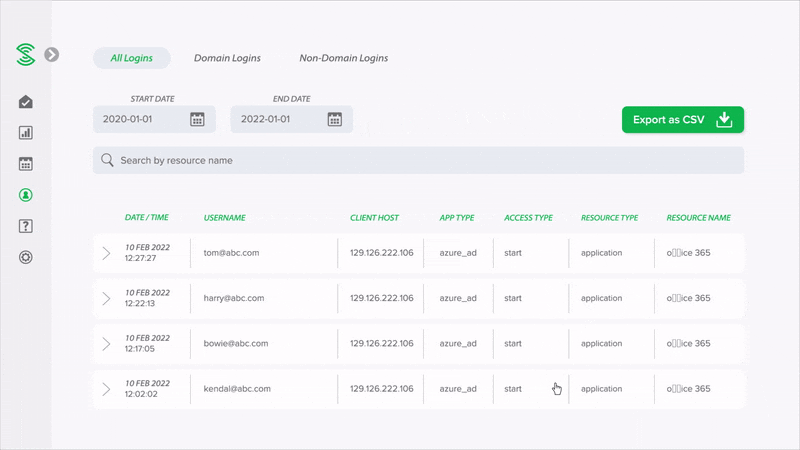
Easy-to-read summary reports, instead of alerts
Monitor your cloud security health with easy-to-read summary reports, without the need to manually go through a high volume of events or alerts. Smart algorithms automatically uncover suspicious activities, and classify user accounts into low, medium or high risk.
Get notified when there is high risk activity
With smart algorithms making sense of activity events, you only get alerted when there is high risk activity, so that you do get swamped by alerts.


Support for 24-mths log storage compliance
For companies that need it, the enterprise edition provides 24 months storage for Microsoft 365 log events, so as to meet compliance.
How is Cloud Security Monitor different?
Conventional Solutions
RAW LOGS
- Report the numerous log events by Microsoft 365 accounts
- Need to manually make sense of large amount of log events or alerts, which is not practical
- Difficult to spot suspicious activities
VS
Monitor for Microsoft 365
SMART REPORTS
- Deploys sophisticated user behavior analytics to detect suspicious user activities
- Automatically makes sense of log events to report high-risk Microsoft 365 accounts
- No need to comb through large amount of log events or alerts
Cloud Security Monitor Use Cases


Suspicious
Login Activity


Privilege
Escalation

Suspicious
Data Access


Unauthorised
Sharing


Unauthorised
Mail Access


Unauthorised
Policy Change
Get a demo today!
Contact our experts with decades of deep and innovative cybersecurity expertise.
Evaluated and accredited by the IMDA to have met its high standards for deployment in large enterprises and government.
InsiderSecurity is 100% made in Singapore.
InsiderSecurity automated monitoring saves us effort and money. We don't have to build or outsource a large IT security team.
Most important of all, we get to sleep better at night.
Jeremy LeeCo-founder of SRX
InsiderSecurity has made it very easy for us to monitor our network traffic, removing the need to laboriously dig through results.
It also gives us the assurance that the websites are well protected.
Tan JinglunIT Director of sgCarMart
InsiderSecurity has cut the monitoring effort from what used to take a few hours a week to around 10 mins.
This is a helpful solution.
Head of ITSingapore Government Statutory Board
InsiderSecurity help us to pick up much more high risk activities, which is not possible with our previous system.
Project ManagerSingapore Government Department
Previous
Next





