Database Activity Monitor
Detect Unauthorized Access
to Your Data
What Database Activity Monitor Does for You?
As data security becomes more and more complex and multi-faceted, protecting all types of data from growing threats across diverse on-premises, hybrid, and public cloud environment can be a daunting task.
Now, state-of-the-art AI-driven and automated Insider Security Monitor – Database Monitoring solution offers a robust real-time data activity monitoring and cognitive analytics that automatically discovers unusual activity around sensitive data. It protects against unauthorized data access by learning normal user access patterns and provides alerts on suspicious activities. The product provides visibility on data activity across all major databases.
Detects Suspicious Activities




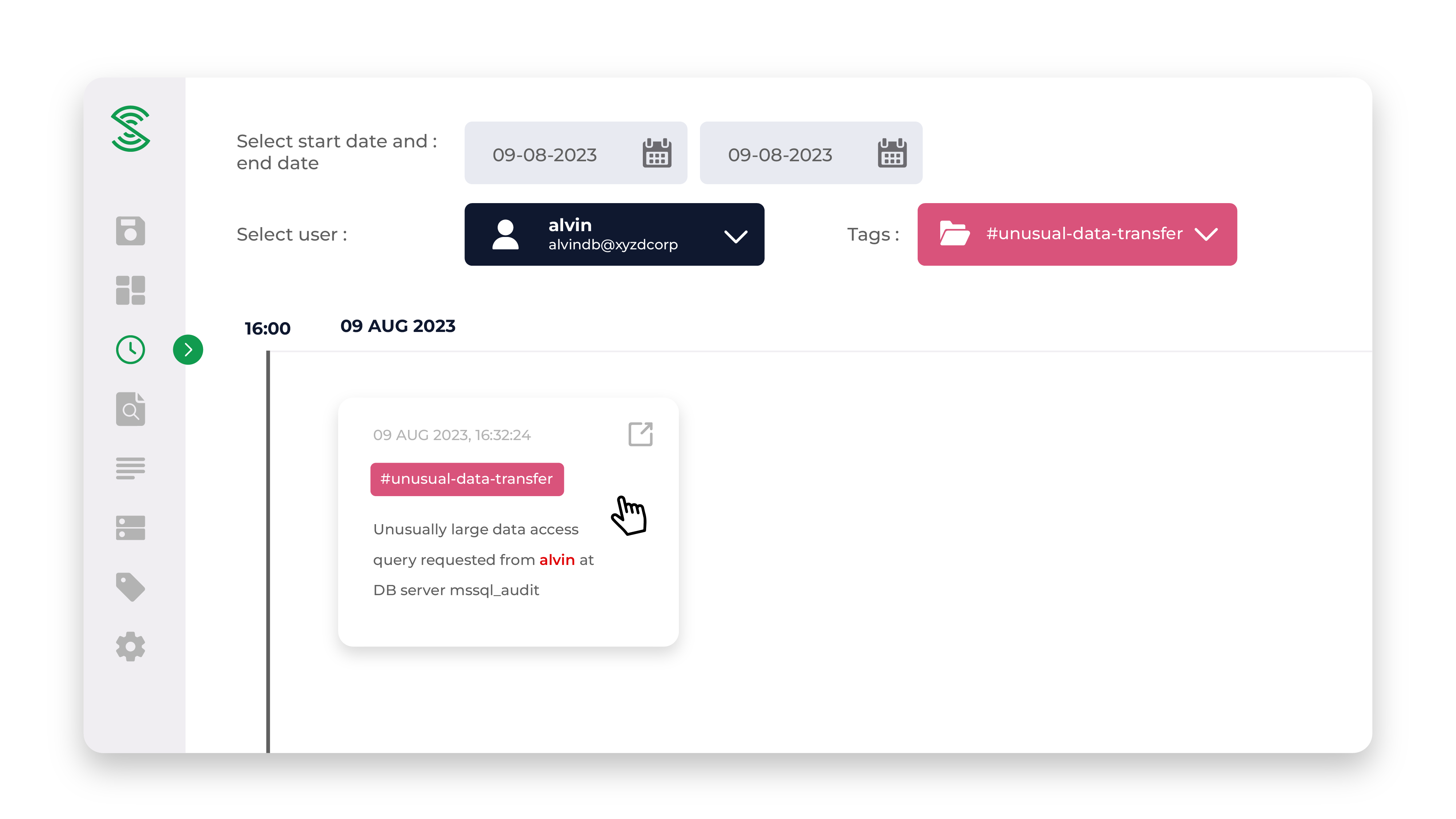

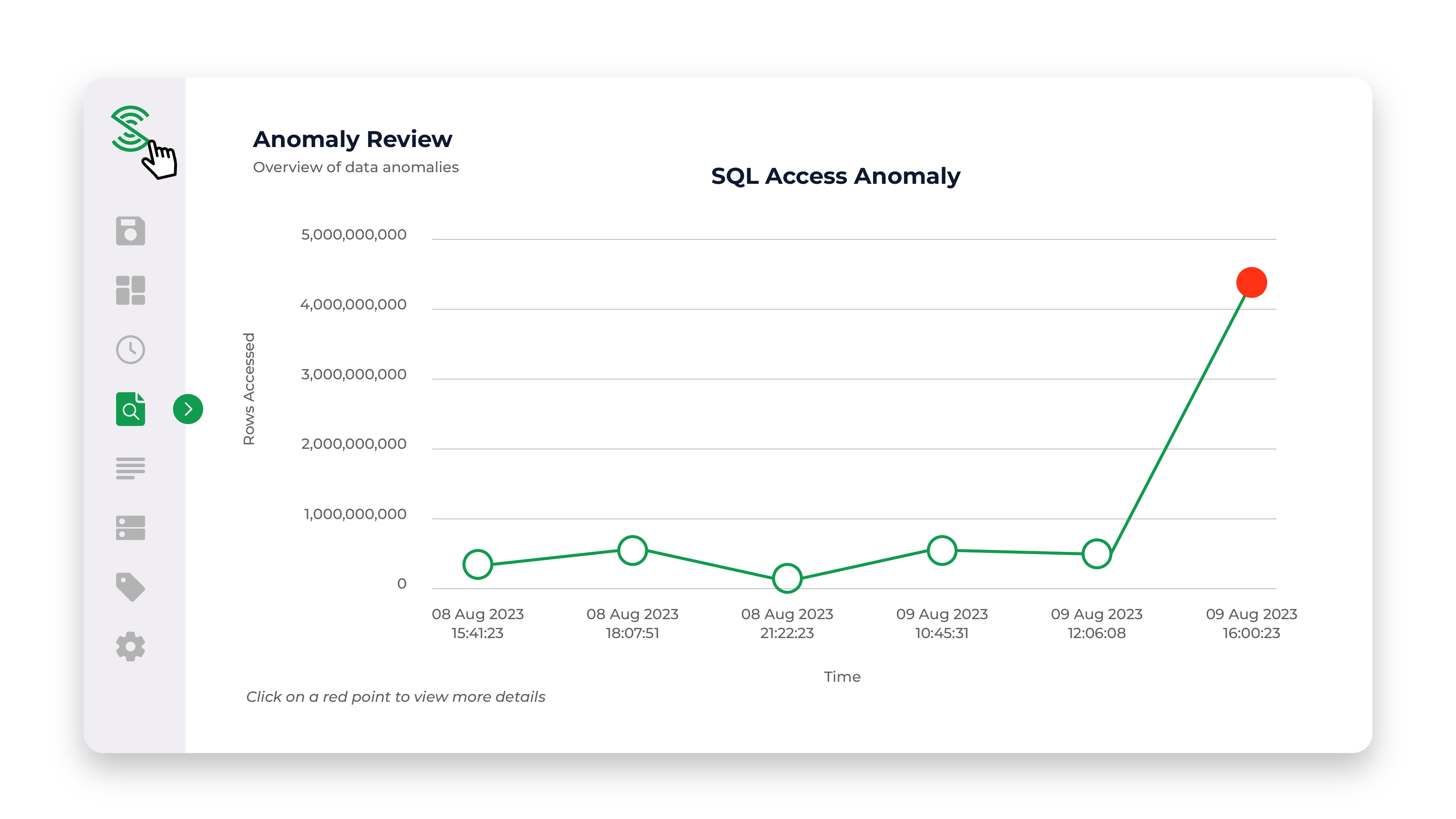



Unusual account login behaviour


Risky administrator commands


Suspicious SQL commands


Unusual data access


Suspicious failed queries


Malicious network traffic in the server,
beyond database traffic
Threat Scenarios


Database account
credentials has been
leaked or stolen


Database is
accidentally left
exposed to the internet


Insider threat


Rogue
administrator


Vulnerable
application that uses
the database


Backdoor installed
in the database
Benefits


Suspicious Database
administrator activity


Suspicious data
access in the database


Unusual network activity
in the database server
Monitor does not require rules to be written/maintained, and significantly reduces the need for manual monitoring and analysis. This enables earlier and greater threat detection.
Evaluated and accredited by the IMDA to have met its high standards for deployment in large enterprises and government.
InsiderSecurity automated monitoring saves us effort and money. We don't have to build or outsource a large IT security team.
Most important of all, we get to sleep better at night.
Jeremy LeeCo-founder of SRX
InsiderSecurity has made it very easy for us to monitor our network traffic, removing the need to laboriously dig through results.
It also gives us the assurance that the websites are well protected.
Tan JinglunIT Director of sgCarMart
InsiderSecurity has cut the monitoring effort from what used to take a few hours a week to around 10 mins.
This is a helpful solution.
Head of ITSingapore Government Statutory Board
InsiderSecurity help us to pick up much more high risk activities, which is not possible with our previous system.
Project ManagerSingapore Government Department
Previous
Next





